Nipper Enterprise for routers, switches & firewalls
Continuous Security &
Compliance Assurance at Scale
Minimizing network infrastructure attack surface with continuous monitoring of routers, switches and firewalls for security control and RMF compliance
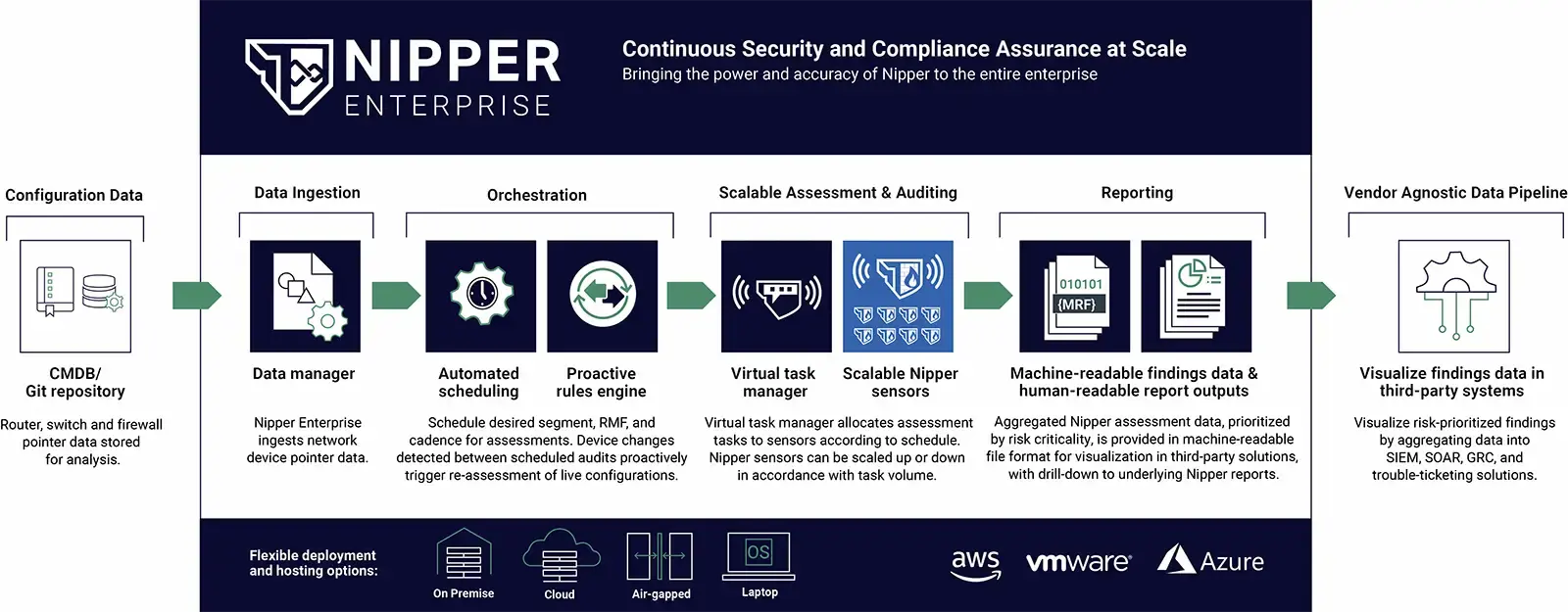
Bringing the Power and Accuracy of Nipper to the Entire Enterprise
Designed to assure network security and compliance, in accordance with vendor device-hardening best practices, Zero Trust segmentation, and control and risk management frameworks - Nipper Enterprise delivers fast, accurate visibility of configuration posture at scale.
Network owners use Nipper Enterprise to increase the coverage and cadence of assessments, evidence continuous compliance with military and industry regulations, and minimize their attack surface via MITRE ATT&CK® misconfiguration prioritization.
Assess network infrastructure
on an enterprise scale
Assure network security &
compliance posture in real-time
Prioritize remediation by risk
to shut-down attack vectors
- Configuration drift detection
- Evidence-based compliance assurance
- Prioritized view of network risk
- Remediation advice to expedite MTTR
- Automated attack vector analysis
Configuration drift detection
Gain immediate awareness of any device configuration changes, providing assurance that planned network changes have not created new vulnerabilities as well as alerting to unplanned changes (indicators of compromise).
Evidence-based compliance assurance
With automated network checks mapped to Risk Management Frameworks (RMFs) and security controls, the solution provides assurance for STIGs, PCI DSS v4.0, NIST SP 800-53, NIST SP 800-171 and CMMC.
Prioritized view of network risk
Nipper Enterprise provides a comprehensive view of prioritized network risk, which considers the impact to the entire network if a misconfiguration is exploited, as well as the ease of exploitation, for an informed view of network risk.
Remediation advice to expedite MTTR
Where possible, device-specific guidance on how to fix misconfigurations – command line scripts in some cases – is provided to inform Plans of Action and Milestones (POAMs) and decrease the mean time to remediate.
Automated attack vector analysis
Minimise the attack surface for network infrastructure and understand exposure to defend against adversary tactics via MITRE ATT&CK misconfiguration prioritization.

SOCs
Automate snapshot views, prioritized for risk, of the security and compliance posture of every router, switch and firewall in a Configuration Management Database (CMDB) on a monthly basis or at a more frequent cadence as required.

NOCs
Check the CMDB for configuration changes and automatically trigger an audit of those changed files for a proactive way to assess the impact of configuration drift as it occurs, without the need for direct, credentialed device access.
Evidence-based:
-
 STIGsAutomate NDM and RTR checks with pass/fail evidence…
STIGsAutomate NDM and RTR checks with pass/fail evidence… -
 NIST SP 800-53Pass/fail evidence of compliance with up to 49 controls…
NIST SP 800-53Pass/fail evidence of compliance with up to 49 controls… -
 PCI DSS 4.0Automate requirement checks for network devices…
PCI DSS 4.0Automate requirement checks for network devices…
Exception-based:
-
 Titania Security AuditDetect where configs deviate from vendor hardening standards...
Titania Security AuditDetect where configs deviate from vendor hardening standards... -
 CISCO PSIRTException-based reports for vulnerabilities…
CISCO PSIRTException-based reports for vulnerabilities… -
 NIST NVDAssess for national vulnerabilities in minutes…
NIST NVDAssess for national vulnerabilities in minutes… -
 CIS BenchmarksCheck for vulnerabilities against the benchmarks…
CIS BenchmarksCheck for vulnerabilities against the benchmarks… -
 NIST SP 800-171*Accurate assessment of up to 89% of network controls...
NIST SP 800-171*Accurate assessment of up to 89% of network controls... -
 CMMC*Assess compliance with up to 89% of network security practices...
CMMC*Assess compliance with up to 89% of network security practices...
*Coming soon
Flexible Deployment
Enterprise Integrations
Stateless & Passive
Proactive Audits
Automatic Labeling
Customizable Scheduling
Configurable Parameters
Agnostic Data Pipeline
Snapshot Reporting
Air-gapped Assessments
Supported Devices
For specific details on Nipper Enterprise's support for vendor’s products, models and versions, please
contact us.









Nipper Enterprise Integrations
eyeExtend Connect for Nipper Enterprise on Forescout Marketplace
This integration combines Forescout's enterprise-wide device visibility and automated incident response capabilities with Nipper Enterprise’s proactive configuration analysis to give NOC and SOC teams near real-time awareness of the impact of every device configuration change on network segmentation and attack surface posture.
ServiceNow CMDB - Nipper Enterprise Integration
The Nipper Enterprise ServiceNow CMDB app, available within the ServiceNow app store, allows Nipper Enterprise users to integrate their ServiceNow CMDB with Nipper Enterprise via an authenticated read only API. This allows the solution to sync and provide continuous, passive and proactive security and compliance assessments of networking devices – giving NOC and SOC teams immediate visibility of configuration drift, complete with automated risk analysis of segmentation and configuration data.
Request a Nipper Enterprise Demo
» Configuration drift prevention
» Critical risk remediation
» Zero Trust networking
» Automated regulatory compliance reporting
» MITRE ATT&CK analysis
» Remediation workflow improvement



.jpg?width=5120&height=2880&name=shutterstock_1590824857%20(2).jpg)