Nipper for routers, switches & firewalls
Accurate Network Device Vulnerability Assessments
Close your most critical security and compliance gaps with risk and remediation findings from Nipper.
Why network devices need Nipper?
The impact of misconfigured routers, switches, and firewalls is global news. Securing these devices to prevent ransomware attacks and delay lateral movement in the event of a perimeter-breach, is essential cyber hygiene.
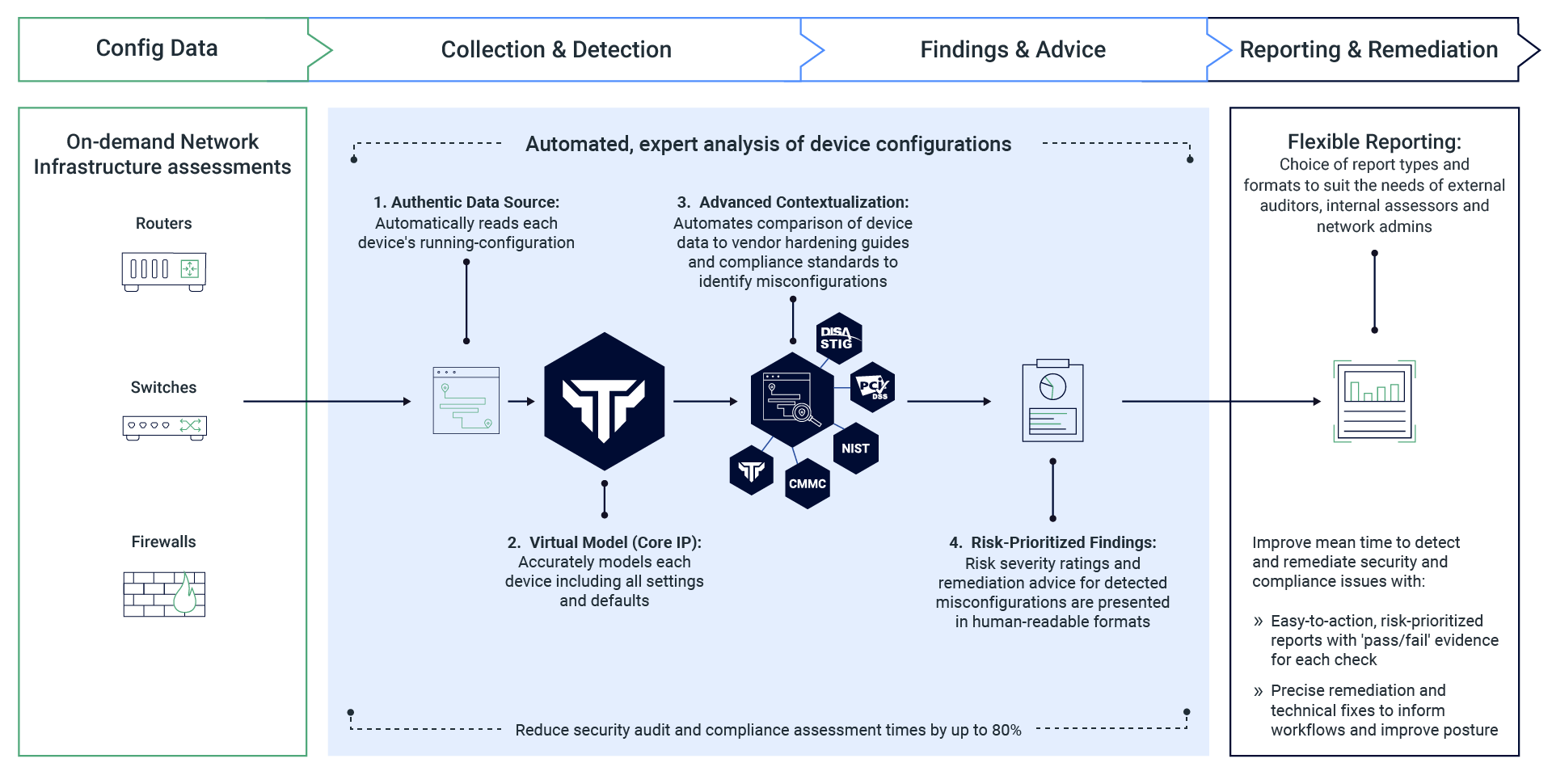
Analyzing device configurations with the precision of a pentester, Nipper is a must have on-demand solution for configuration management, compliance and control.
Network risk owners use Nipper to shut down known pathways that could allow threat actors to alter network configurations and scale attacks.
Whilst assessors use Nipper to reduce audit times by up to 80% with pass/fail evidence of compliance with military, federal and industry regulations.
Assess devices even in air-gapped and offline environments
Validate device security using vendor hardening standards
Prioritize vulnerability remediation by impact of exploitation
Evidence compliance with risk management frameworks
Risk-Based Vulnerability Management for Network Devices
Providing complementary analysis to server-centric vulnerability assessment, Nipper’s advanced network contextualization suppresses irrelevant findings, prioritizes risks by criticality, and automates device-specific guidance on how to fix misconfigurations.
- Exception-based security reporting
- Evidence-based compliance reporting
- Risk-prioritized view of non-compliances
- Remediation analysis to improve compliance posture
Exception-based security reporting
Nipper’s renowned Security Audit automates configuration checks to report exceptions that fail to adhere to vendor hardening guides and network infrastructure hardening best practices.
Evidence-based compliance reporting
Providing specific information about the tests performed, Nipper checks whether each configuration passes or fails to comply with the assessors chosen RMF control or security standard.
Risk-prioritized view of non-compliances
Prioritizing findings by compliance risk, Nipper visualizes the significance of its findings according to CVSS, STIG, Cisco SIR, and its own trusted risk criticality rating systems.
Remediation analysis to improve compliance posture
Device-specific guidance on how to fix misconfigurations – including command line scripts in some cases – is provided to decrease the mean time to remediate security and compliance risks and inform POAMs.

Internal and External Security Teams
Quickly, easily and accurately detect networking misconfigurations and determine their impact if exploited, the ease of exploitation, and ease of fix. View the findings through Nipper’s security or compliance lenses to accurately report your posture and prioritize remediation workflows by risk criticality.

Compliance Auditors and Pentesters
Significantly reduce the time spent auditing routers, switches and firewalls against industry and regulatory compliance standards by automating the in-depth configuration analysis and recommendation reporting which can be white-labelled for your branding.
Evidence-based:
-
 STIGsAutomate NDM and RTR checks with pass/fail evidence…
STIGsAutomate NDM and RTR checks with pass/fail evidence… -
 PCI DSS 4.0Automate requirement checks for network devices…
PCI DSS 4.0Automate requirement checks for network devices… -
 NIST SP 800-53Pass/fail evidence of compliance with up to 49 controls…
NIST SP 800-53Pass/fail evidence of compliance with up to 49 controls… -
 NIST SP 800-171Accurately assess compliance with network controls...
NIST SP 800-171Accurately assess compliance with network controls... -
 CMMCAccurately assess compliance with network security practices...
CMMCAccurately assess compliance with network security practices...
Exception-based:
-
 Titania Security AuditDetect where configs deviate from vendor hardening standards...
Titania Security AuditDetect where configs deviate from vendor hardening standards... -
 CISCO PSIRTException-based reports for vulnerabilities…
CISCO PSIRTException-based reports for vulnerabilities… -
 NIST NVDAssess for national vulnerabilities in minutes…
NIST NVDAssess for national vulnerabilities in minutes… -
 CIS BenchmarksCheck for vulnerabilities against the benchmarks…
CIS BenchmarksCheck for vulnerabilities against the benchmarks…
“Nipper plays an important role as it helps to audit every device accurately and enables us to dedicate our valuable resources by analyzing and prioritizing fixes.”
Senior Analyst, Retail

“It provides best services in its class by discovering vulnerability in routers, switches and firewalls and automatically prioritizes risks to organization. Its virtual modelling is one of the best features that provides exact fixes by reducing false positives and helps us to be secure and compliant.”
IT Services Industry

“We have been using Titania Nipper for many years now in our business unit and we find the product very useful in maintaining our regulatory and contractual requirements. We are using Titania Nipper for our network devices which enables us to identify non-compliance in our network devices configurations.”
Information Security Operations, IBM

“What I love about Nipper, especially when it comes to PCI, is that it gives you recommendation distinctions where it says ‘here are the areas where you might want to look’. That’s how we found out that local account passwords in our routers weren’t adequate.”
Security Risk Management, Telecommunications

“The biggest advantage I find with Nipper is the speed of response… in terms of speed of getting results and getting a quick overview it’s fantastic. There’s nothing else like it out there as far as we’re aware.”
International Logistics Facility

How it Works
How to use Titania Nipper: Nipper is a downloadable application which is installed on a local machine, enabling deployment in air-gapped environments and offline networks. The configuration assessment methodology does not require direct access to devices. Running the latest available version of Nipper ensures access to the most up to date security policy checks, compliance framework mapping and product enhancements.
Audit Scoping
Configurable Check Parameters
Report Browser
'Save' Formatting
Air-gapped Assessments
Nipper Supported Devices
For specific details on Nipper’s support for vendor’s products, models and versions, please either contact us or request a trial.









On-demand security & compliance assessments by Nipper
Close your most critical security and compliance gaps. Find out how Nipper can help with on-demand, risk-based network device configuration assessments.

Nipper Product Overview - Risk-based Vulnerability Management
Delivering security from compliance - Automating accurate, on-demand router, switch and firewall configuration security assessments with Nipper.

Introduction to Nipper for risk-based vulnerability management
In this webinar, we’ll introduce Nipper and show you how to automate accurate, on-demand security assessments for routers, switches, and firewalls.
Need continuous network monitoring to get ahead of threat actors and configuration errors?
Nipper Resilience gives you real-time visibility and proactive analysis of every network change, to improve the readiness, resilience and recoverability of your critical systems.
Request a Nipper Demo
- Evidence-based compliance reporting
- Security audits and vulnerability management
- Risk-prioritized view of non-compliances
- Remediation analysis to improve compliance posture