In an ideal world, all your critical data and the devices protecting it would be disconnected from the rest of the world, air-gapped, in a bunker under a mountain guarded by security detail. That way you know it is secure. If it’s not connected, then how can a remote attacker gain access?
But we don’t live in an ideal world, so in practice the systems with critical data are not only fed by other systems but often push to other systems so they do need to be connected. However, they only need to be connected to what is essential for operation. This is a key part of effective segmentation, and fundamental to zero trust principles.
“Zero-Trust Segmentation (ZTS) isolates critical resources so that if a network is compromised, the attacker can’t gain access.” Forrester
For example, does the laptop used by an employee from Human Resources for their day-to-day work need to be connected physically to the same network that houses or has access to a more secure segment, such as a Cardholder Data Environment (CDE)?
The ultimate mitigating control is to physically separate these segments. If the HR laptop becomes infected with a modern variant of ransomware, it cannot move laterally to more critical areas of the network such as the CDE.
Network Infrastructure Topology
Let’s imagine for a second that you are already breached - what does your Network Infrastructure Topology look like?
|
Is everything flat? If an attacker lands on a machine on the network, this leaves them only one hop away from the CDE and also exposes a huge attack surface to deploy an attack such as ransomware with a greater impact. |
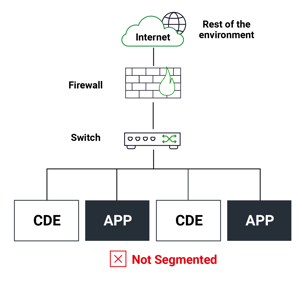 |
|
Are some parts of the network like the CDE for instance isolated and segmented but everything else remains flat? Leaving a minimal attack surface for the CDE but a large remaining attack surface for the rest of the organization's network. |
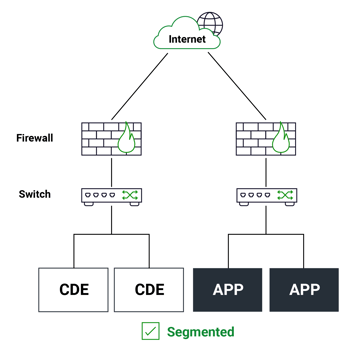 |
|
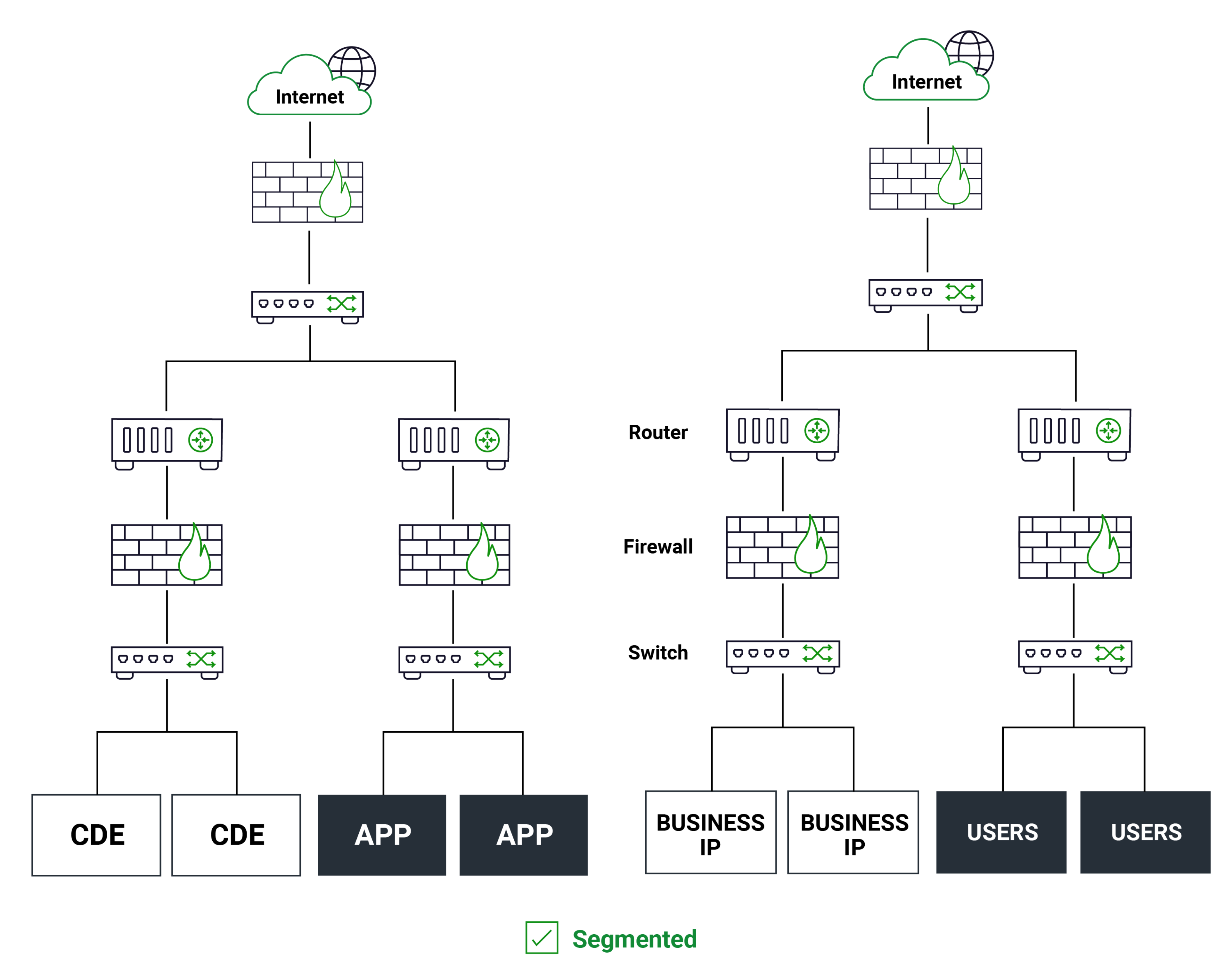
Is everything isolated and segmented according to network function? Thus keeping the attack surfaces as minimal as physically possible to support the organization’s operation. If it’s not physically connected in some way, the attacker cannot get to it. |
|
How secure is that segmentation?
Could that attacker access that firewall, escalate their privileges and open up a route from that segment to the CDE? What about beyond the CDE? Is every router, switch and firewall on the network secure?
Just by doing this, we have already started look at things through an attacker’s lens and highlighting the criticality of certain devices such as routers, switches and firewalls in protecting and controlling access to CDE.
ZT Effective Network Segmentation gives you:
- A reduction of attack surface – reducing the area open to potential threat.
- Containerisation of a threat thereby preventing the proliferation of an attack such as ransomware.
- Easier to implement access controls and a reduction in the organization’s exposure to insider threat.
- Full control over operational bandwidth.
Organizations that have adopted ZTS save an average of $20.1m in application downtime and deflect five cyber disasters per year.Venture Beat
Router, Switch and Firewall Compliance
Zero Trust Segmentation is absolutely critical in attack prevention and prevention of attack proliferation - containerizing the threat and preventing unwanted privilege escalation & lateral movement across the network. But effective network segmentation relies on the security and compliance of every router, switch and firewall. To see how Nipper and Nipper Resilience can support this visit our solutions section.
Zero Trust Segmentation and Attack Surface Management
Effective segmentation is reliant on effective attack surface management, which comprises:
- Asset discovery – ultimately you want to know what is on your network at any point in time.
- Asset validation – should it be on your network? If it shouldn’t be, you want to remove it.
- Asset inventory – if it should be on your network, it should be logged for analysis and assessment
- Asset assessment – The security and compliance posture should be checked to ensure that it should continue to remain on the network.
This approach ensures we're looking at our networks, considering them from all angles, the way that an attacker would. It can help target remediation effort and resource – using threat intelligence to inform risk prioritization and remediation, allowing organizations to view what is most critical to them but also what is most likely to be exploited right now.
To learn more about how Nipper Resilience can support asset assessment, watch Ian Robinson, Chief Architect at Titania talks through this and how Nipper Resilience enables the shift from ad-hoc, sampled assessments to continuous compliance assurance for the Enterprise.


.png?width=350&name=Social%20and%20blog%20header%20images%20(7).png)



