Reasons why Nipper Resilience should be a part of your cybersecurity tech stack, to help assure effective network infrastructure segmentation at scale for PCI DSS compliance.
Determining compliance with PCI DSS
When the latest iteration of PCI DSS (Payment Card Industry Data Security Standard) 4.0 was released almost two years ago, the end of the transition period to update security controls to conform to this version of the standard seemed a long way off. Now with v3.2.1 being retired on 31 March 2024, ensuring compliance with PCI DSS v4.0 has become of increasing importance.
A key part of this will require taking a zero-trust approach to continuously verifying device security; never trusting that your devices have remained secure, and your networks adequately segmented, because what was secure yesterday at the point of audit may no longer be secure today.
This is where Nipper Resilience can help.
Historically, achieving PCI DSS compliance has involved laborious manual mapping of network infrastructure device checks to specific requirements. This can be a time-consuming and error-prone process. Nipper Resilience accurately determines compliance with PCI DSS requirements for routers, switches and firewalls, acting with the precision of a pen tester at scale, as well as running regular automatic assessments to detect non-compliances, reducing the risk to the Cardholder Data Environment (CDE). So, at the point of an audit, you can evidence your compliance with the standard and detect any instances where there are non-compliances and your CDE is at risk.
Nipper Resilience can seamlessly sync with many CMDB or Configuration Repositories to segment data, classifying device references in minutes. For instance, in as little as 3 minutes our solution can sync up to a Service Now CMDB containing 10,000 devices, or 100,000 in just 10 minutes, and so on. The platform will inherit all segmentation meta data and taxonomy mapping for these devices, and this is all done passively as it is performing its assessments from what is in the CMDB, so Nipper Resilience does not affect the operational bandwidth of your critical network.
Then when those configurations are synced, to ensure consistent compliance, you can effortlessly schedule PCI DSS assessments of your CDE network infrastructure in three simple steps:
1. Firstly, identify the segment you want to assess.
2. Secondly, choose what assessment to perform on that segment’s devices (e.g. PCI DSS).
3. Finally, set your cadence and control how frequently this assessment should be carried out throughout the year (e.g. quarterly to support PCI DSS evidence for audit, or as continuously as daily to drive security from compliance)
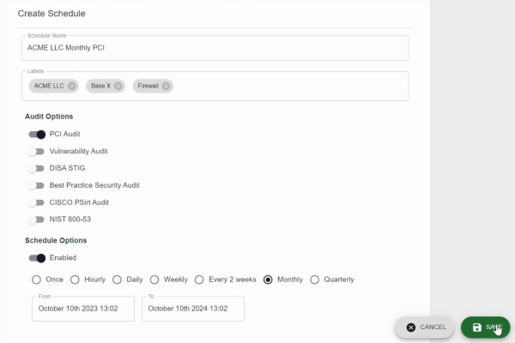
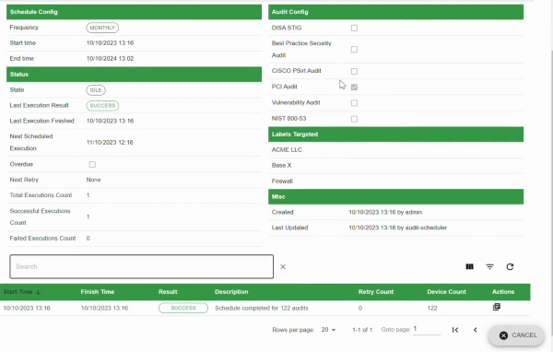
These schedules then perform the assessments at the set cadence and all the evidence is collected and consolidated, which can then be pushed to various platforms such as a SIEM (e.g. Elastic or Splunk). Whilst not all non-compliances are equal through an attacker's point of view, Nipper Resilience enriches the data being pushed to these platforms with various risk lenses, allowing you to risk prioritize your posture views and your remediations accordingly.
The importance of proactive assessment and effective incident response
Whilst automating the PCI DSS 4.0 requirements relevant for network devices on the CDE segments on a daily basis is possible with Nipper Resilience, this generates a lot of repetitive data, and which may make it harder for you to find the critical information that you really need. You should strongly consider the typical frequency of changes to networking device configurations, as alterations, whether accidental or nefarious, may introduce vulnerabilities.
Assessing devices after they have been altered is important as these changes show us what the typical frequency of changes to networking device configuration is, but most importantly identify as an indicator of compromise, therefore informing incident response to help shut down that threat in good time.
Additionally, internal threats such as disgruntled employees or those seeking to expose valuable data for financial gain, should not be overlooked. Vigilance is crucial to detect and address potential risks originating from within the organization. For example, an attacker might focus on non-repudiation by disabling audit logging to conceal their next phase of their attack, which might be to manipulate firewall rules or create new interfaces to access the CDE segment. They are likely to start with the first phase and then wait to see how effective an organization's incident response is before proceeding.
Proactive assessment with Nipper Resilience provides visibility of change, reporting any non-compliance with PCI DSS 4.0 requirement 10.x, by detecting changes in the CMDB and applying and following a configurable set of rules, such as “as soon as a device in the CDE segment has changed, performs a PCI DSS 4.0 assessment.”
Therefore, continuous assessment is incredibly important for ensuring your organizations security and can be achieved in a practical way by monthly or quarterly scheduled assessments from a zero-trust perspective, along with proactive assessment of devices as and when their configurations change.

Using threat intelligence to inform risk prioritization and remediation
However, you can take proactive assessment to the next level with Nipper Resilience, by using threat intelligence to really inform your risk prioritization and remediation workflows, and proactively improve your compliance posture.
Whilst Zero Trust effective network segmentation reduces the attack surface, attack frameworks provide additional risk lens and threat intelligence to better understand what exposure there is on these attack surfaces. Understanding how adversaries operate is key and essential to assessing risk, exposure to attack, prioritization and remediation of networking devices and protecting critical areas of your network, such as the CDE.
This intelligence is vital for targeting your remediation effort and resource and for risk prioritization, as it allows organizations to view what is most critical to them but also what is most likely to be exploited right now.
Most organizations may be tasked with tens of thousands of vulnerabilities on their networking devices due to out-of-date software, but patching every one of those devices would be extremely time consuming and will likely affect operation. So, organizations should start with those vulnerabilities that are known to be active threats at the time, rather than attempting to resolve all vulnerabilities with the same priority.
By looking closely at what techniques and tactics are being used in the wild by threat actors and threat groups, it allows organizations to reflect on whether they are doing all they can to prevent privilege escalation and what their current risk posture to certain techniques is looking like. Keeping track of these techniques and tactics, who is using them and what industries they are targeting can help organizations to isolate and report on exposure to these.
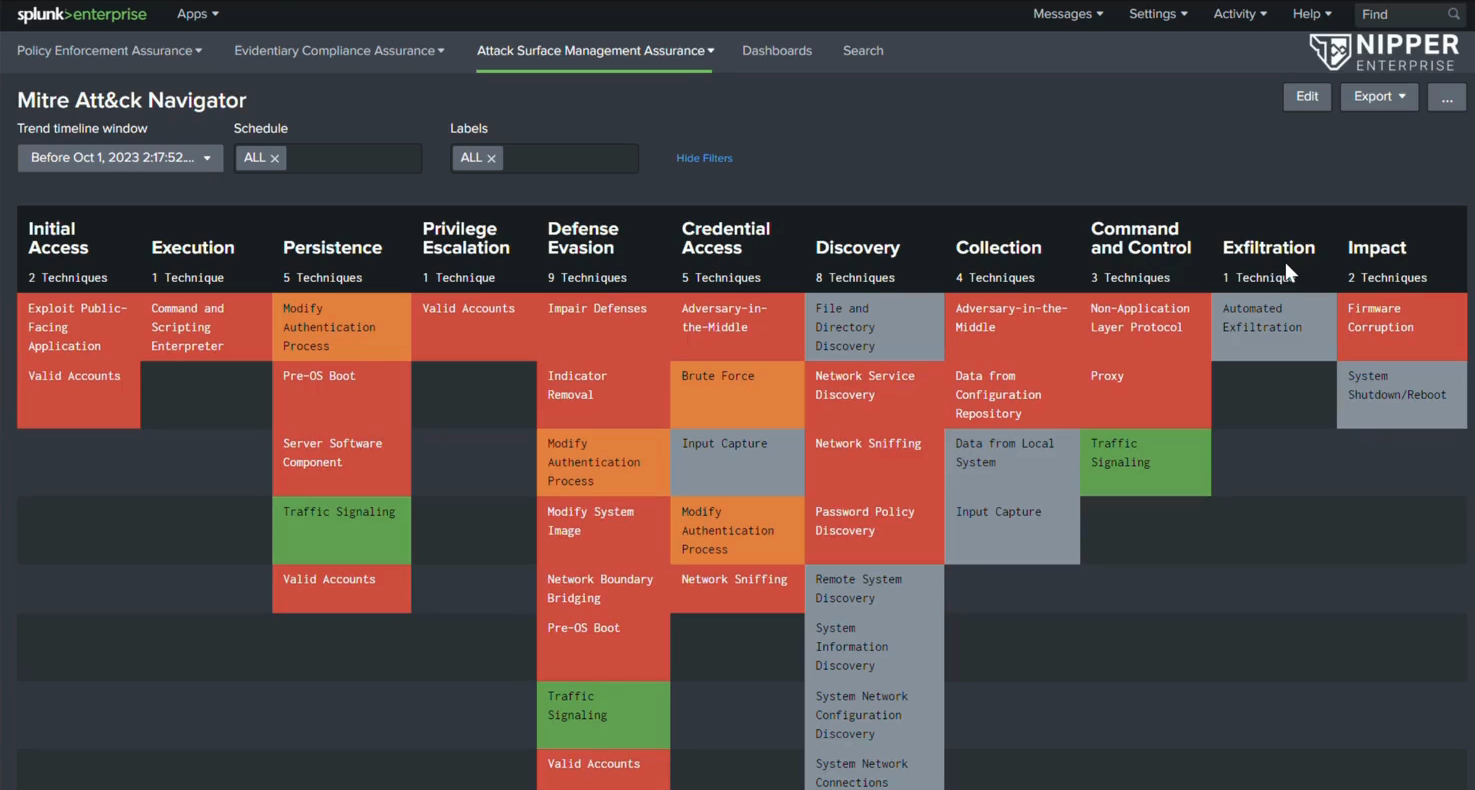
Whilst organizations like Mitre do exactly this and provide the necessary intelligence, Nipper Resilience can then augment the data using this intelligence to give organizations the power to answer these important questions and defend themselves by looking through an attacker’s lens. This creates a very powerful dataset to feed into risk prioritization and remediation plans.
To learn more about how Nipper Resilience can help your organization to determine compliance with PCI DSS, reduce attack surface with effective segmentation at scale and use threat intelligence to inform your risk prioritization and remediation workflows, watch this video of Ian Robinson, Chief Architect at Titania, demonstrating the importance of continuously viewing and managing PCI DSS Compliance through an attacker's lens.
Request a demo
Our solution can be used to increase the coverage and cadence of assessments, evidence continuous compliance with industry regulations, and minimize attack surface via Mitre ATT&CK misconfiguration prioritization.
If you would like to see for yourself how Nipper Resilience can help you to assure effective network infrastructure segmentation at scale, then request a live demonstration with one of our experts today.






